Cloud
This screen allows configuring a cloud trigger based on Amazon Simple Queue Service (SQS), integrating automated bots with AWS queues for task execution.
There are 2 types of AWS triggers:
- SQS: Monitors a specific SQS queue and triggers the bot when a new message is received.
- S3: Monitors an S3 bucket for events like file uploads and triggers the bot in response to these events.
Note
To use these triggers, you need an AWS account with appropriate permissions to access SQS and S3 services. Additionally, AWS credentials (Access Key and Secret Key) must be configured as environment variables to make selection during the trigger configuration process.
SQS
Below is the description of the fields needed to configure an SQS type trigger.
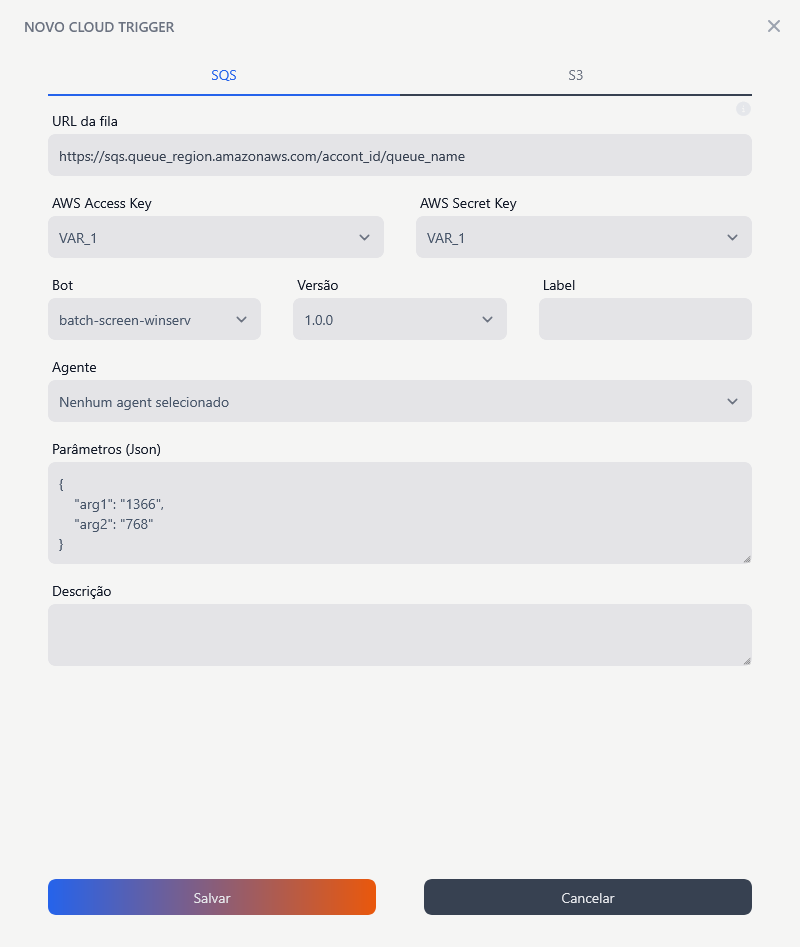
Configuration Fields
Queue URL
- Expected format:
https://sqs.<queue_region>.amazonaws.com/account_id/queue_name - Description: Complete address of the SQS queue that will be monitored to trigger the event.
AWS Access Key
- Description: AWS access key with permissions to access the SQS queue.
- Example:
AWS_ACCESS_KEY - Important: This key must be previously configured as an environment variable in the system variables section.
AWS Secret Key
- Description: AWS secret key corresponding to the access key.
- Example:
AWS_SECRET_KEY - Important: This key must be previously configured as an environment variable in the system variables section.
Bot
- Default value: First from the list of available bots
- Description: Bot that will be executed when the trigger is fired.
- Important: The bot must be previously created and available on the platform for selection.
Version
- Expected value:
X.Y.Z(example:1.0.0) - Description: Specific version of the bot to be used.
- Important: There is an option to select the bot’s
releaseversion, which will always use the latest available version.
Label
- Description: Optional identifier for the trigger. Can be used for organization or filtering.
Agent
- Current value: Select an agent from the list
- Description: Defines the agent responsible for bot execution.
- Important: The agent must be active and connected to make selection during scheduling. Possibility to define multiple agents for the same schedule, avoiding execution bottlenecks.
Parameters (JSON)
- Description: Allows entering additional parameters for the bot, in JSON format.
{
"arg1": "1366",
"arg2": "768"
}Description
- Description: Field to provide a detailed description of the trigger, facilitating identification and understanding of its purpose.
Permissions
For the trigger to work correctly, the SQS queue must have a permissions policy that allows the platform service to access and read messages. The policy must include the following statement:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "SQSSpecificQueue",
"Effect": "Allow",
"Action": [
"sqs:CreateQueue",
"sqs:DeleteQueue",
"sqs:TagQueue",
"sqs:ListQueues",
"sqs:SetQueueAttributes",
"sqs:ReceiveMessage",
"sqs:DeleteMessage"
],
"Resource": [
"arn:aws:sqs:${Region}:${Account}:${QueueName}"
]
}
]
}Note
Replace ${Region}, ${Account} and ${QueueName} with the actual values of the queue you want to monitor.
If you want to monitor multiple queues, use "Resource": ["*"], but be aware of associated security risks.
S3
Below is the description of the fields needed to configure an S3 type trigger.
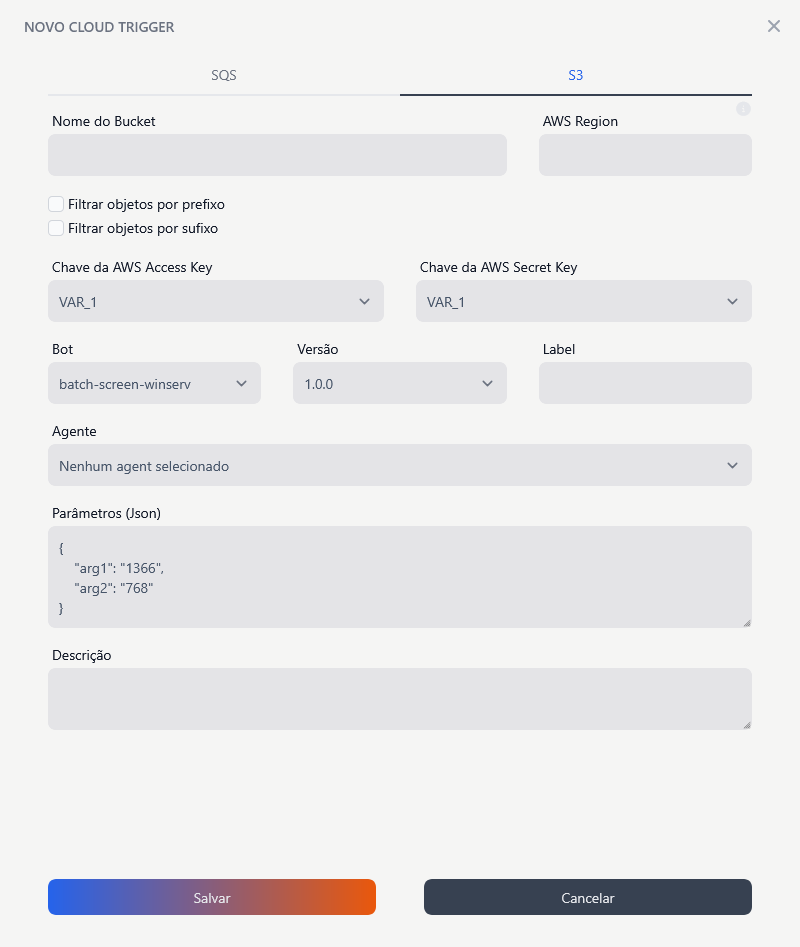
Configuration Fields
Bucket Name
- Description: Exact name of the S3 bucket that will be monitored for events.
AWS Region
- Description: AWS region where the bucket is located (e.g.,
us-east-1,sa-east-1).
Filter objects by prefix
- Description: Allows triggering only for objects whose name starts with the specified prefix.
Filter objects by suffix
- Description: Allows triggering only for objects whose name ends with the specified suffix (e.g.,
.csv,.jpg).
AWS Access Key
- Description: AWS access key with permissions to access the SQS queue.
- Example:
AWS_ACCESS_KEY - Important: This key must be previously configured as an environment variable in the system variables section.
AWS Secret Key
- Description: AWS secret key corresponding to the access key.
- Example:
AWS_SECRET_KEY - Important: This key must be previously configured as an environment variable in the system variables section.
Bot
- Default value: First from the list of available bots
- Description: Bot that will be executed when the trigger is fired.
Version
- Expected value:
X.Y.Z(example:1.0.0) - Description: Specific version of the bot to be used.
Label
- Description: Optional identifier for the trigger. Can be used for organization or filtering.
Agent
- Current value: Select an agent from the list
- Description: Defines the agent responsible for bot execution.
Parameters (JSON)
- Description: Allows entering additional parameters for the bot, in JSON format.
{
"arg1": "1366",
"arg2": "768"
}Description
- Description: Field to provide a detailed description of the trigger, facilitating identification and understanding of its purpose.
Permissions
For the trigger to work correctly, the S3 bucket must have a permissions policy that allows the platform service to access bucket events. The policy must include the following statement:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "S3BucketLevel",
"Effect": "Allow",
"Action": [
"s3:ListBucket",
"s3:GetBucketPolicy",
"s3:GetBucketNotification",
"s3:PutBucketNotification"
],
"Resource": [
"arn:aws:s3:::${BucketName}/${KeyName}"
]
},
{
"Sid": "S3ObjectLevel",
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:PutObject",
"s3:GetObjectVersion",
"s3:PutObjectAcl",
"s3:PutObjectTagging"
],
"Resource": [
"arn:aws:s3:::${BucketName}/${KeyName}"
]
}
]
}Note
Replace ${BucketName} and ${KeyName} with the actual values of the bucket and prefix/suffix you want to monitor.
Complete IAM Policy
Create an IAM user with the policy below to allow the trigger to work correctly with both S3 and SQS services.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "S3BucketLevel",
"Effect": "Allow",
"Action": [
"s3:ListBucket",
"s3:GetBucketPolicy",
"s3:GetBucketNotification",
"s3:PutBucketNotification"
],
"Resource": [
"arn:aws:s3:::${BucketName}/${KeyName}"
]
},
{
"Sid": "S3ObjectLevel",
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:PutObject",
"s3:GetObjectVersion",
"s3:PutObjectAcl",
"s3:PutObjectTagging"
],
"Resource": [
"arn:aws:s3:::${BucketName}/${KeyName}"
]
},
{
"Sid": "SQSSpecificQueue",
"Effect": "Allow",
"Action": [
"sqs:CreateQueue",
"sqs:DeleteQueue",
"sqs:TagQueue",
"sqs:ListQueues",
"sqs:SetQueueAttributes",
"sqs:ReceiveMessage",
"sqs:DeleteMessage"
],
"Resource": [
"*"
]
}
]
}Note
Replace ${BucketName} and ${KeyName} with the actual values of the bucket and prefix/suffix you want to monitor.